[ad_1]
Head over to our on-demand library to view sessions from VB Transform 2023. Register Here
The rapid rise in cyberattacks delivering malicious payloads, including ransomware, happens because organizations have become too complacent with legacy IAM, VPN, and perimeter-based network security systems. CISOs tell VentureBeat that hardware-based systems, never designed to protect beyond perimeters, can’t identify the latest ransomware and malware-free attacks and have now become a liability.
Proving how lethal it is to rely on legacy technology that can’t identify the latest threats, CrowdStrike’s latest research found that 71% of all detections indexed by CrowdStrike Threat Graph are malware-free.
From attackers acting alone to large-scale operations financed through organized crime and nation-states, every attacker knows that legacy VPN, endpoint, and perimeter systems can’t see a malware-free attack, their attack strategies or their payloads.
The more siloed security systems are, the greater the probability that an attacker gets in and stays undetected, in some cases for years, because an organization trusted in perimeter security for too long and got compromised. Primary targets that attackers go after today include healthcare and manufacturing because even the slightest slowdown could cost lives and potentially destroy the business.
Event
VB Transform 2023 On-Demand
Did you miss a session from VB Transform 2023? Register to access the on-demand library for all of our featured sessions.
Forrester’s recent report, The Zero Trust Edge Solutions Landscape, Q2 2023, provides insights and useful analysis of how CISOs can migrate away from risky legacy tech stacks that rely on outdated perimeter security approaches and better secure their IT infrastructure with Zero Trust Edge (ZTE). Forrester’s study reveals that the key drivers behind ZTE adoption include the shift to remote work and distributed assets, increased business speed and disruptive vendors offering integrated network/security, along with profiles of 22 of the leading vendors in the market.
Barracuda Networks, Cato Networks, Cisco Systems, Cloudflare, Cradlepoint, Forcepoint, Fortinet, Google, HPE Aruba Networking, Huawei, iBoss, Juniper Networks, Lookout, Menlo Security, Netskope, Nokia, Open Systems, Palo Alto Networks, Sophos, Versa Networks and VMware Zscaler are included in the report.
Closing Cloud, IoT, and remote-work gaps need to happen now
Attackers are out-innovating enterprises where it matters most, starting with endpoints and progressing to taking control of identities and privileged access credentials. Gaps in legacy tech stacks, long known internally within organizations but not a priority to fix, are just as much to blame as the growing sophistication of social engineering techniques, including the rising popularity of pretexting that attackers use to defraud victims.
Attackers know that IT teams struggle to get cloud configuration right, often leaving entire instances and accounts open. IoT is another trouble spot; remote access opened the door to thousands of organizations getting hacked globally.
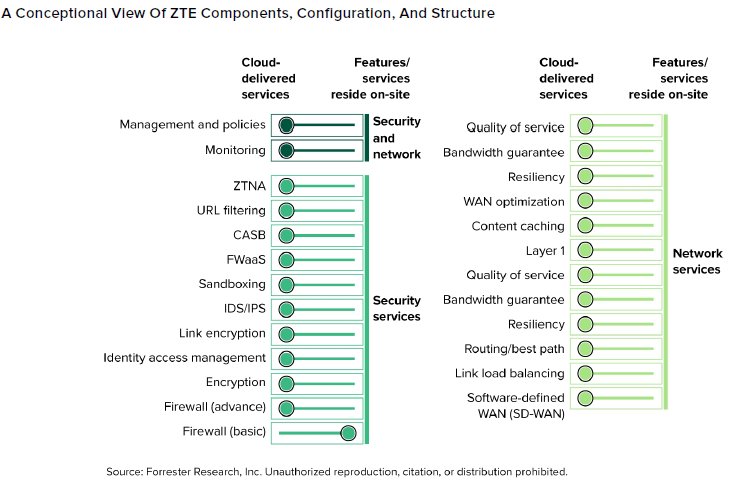
The Zero Trust Edge (ZTE) design goals center on providing tech stack consolidation, reducing risks and costs and increasing visibility and control across IT infrastructures. ZTE is gaining adoption with CISOs whose highest priority, in many cases, is to consolidate from too many vendors while increasing efficacy and strengthening security postures. The goal CISOs are after is to trim back the number of firmware- and hardware-based legacy systems they have, in addition to software-defined wide area networking (SD-WAN), secure web gateway (SWG) and cloud access security broker (CASB) vendors into a more integrated, adaptive architecture supported by a core set of vendors.
Defining Zero Trust Edge
Forrester defines ZTE as “a solution that combines security and networking functionalities — such as software-defined WAN (SD-WAN), cloud access security broker (CASB), Zero Trust network access (ZTNA), and secure web gateway (SWG) — that a single vendor can deliver and support in any combination of cloud, software, or hardware components.” Leading use cases include improving application performance, cloud secure access, visibility, and cloud management require integrated networking and security.
Forrester’s analysts write, “ZTE is a disruptive and high-stakes architecture,” referring to ZTE’s ability to solve several significant problems while simultaneously consolidating four core technologies into a unified architecture solution.
Early ZTE pilots are showing strong results in securing remote workforces, improving remote site security and dependability through multiple connectivity options, streamlining networking and providing more streamlined security management. CISOs and their teams running pilots say that transitioning ZTE’s discrete components to cloud-based managed and monitored services is helping free up localized hardware and system to optimize workloads further locally.
ZTE is the revenue engine cybersecurity vendors need
ZTE presents a significant opportunity for cybersecurity vendors to drive new revenue growth by selling tech stack consolidation. CISOs tell VentureBeat that legacy network security approaches have failed to adequately secure today’s distributed environments with remote workers and cloud-based resources. One CISO confided to VentureBeat that legacy perimeter systems are just like not having a system installed at all because it’s beyond the point of stopping attacks invented less than a year ago.
Legacy network approaches have created gaps in organizations’ ability to secure resources, continually improve efficiency and keep up with the speed required to capitalize on new digital business initiatives. ZTE focuses on these challenges by converging security and networking tools into integrated, cloud-delivered architecture.
According to Forrester’s ZTE research, top vendors are capitalizing on ZTE’s potential to consolidate point solutions into a single offering consumed as a service. This aligns with CISOs’ buyer preferences for reduced complexity and operating expense (OPEX) models.
An estimated 78% of organizations prefer to buy or consume consolidated functionalities as a service, according to Forrester’s Security Survey, 2022. Forrester’s analysts observe that the top vendors are ambitious regarding their plans to offer an entire turnkey package, adding that “the idea of having a single architecture for all security solutions on an opex basis will be compelling for the SMB/midmarket.” Forrester cautions that vendors offering ZTE are still overcoming limitations in their core areas.
With tech stack consolidation a priority for CISOs, ZTE shows potential to be the next viable evolution of security infrastructure. CISOs running pilots tell VentureBeat that ZTE is delivering measurable gains in operations performance, more effective endpoint and identity security and lower costs due to standardizing on a unified architecture. The market dynamics make clear that ZTE is the new revenue engine cybersecurity vendors need.
Top ZTE use cases
Forrester identified the six core use cases where ZTE delivers the most value. Underscoring them all is a strong focus on achieving greater cyber-resilience while improving network performance and reliability.
CISOs from banking and financial services tell VentureBeat that ZTE’s use case of delivering cloud-secure access and securing virtual work teams using Zero Trust Network Access (ZTNA) is a part of their pilots today. Every pilot VentureBeat has learned about is running real-time visibility and history network statistics to quantify visibility and observability gains.

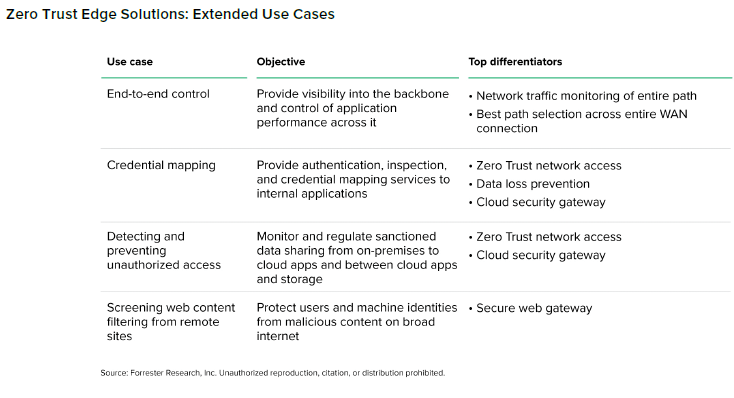
In addition to the core use cases, Forrester identified four extended Zero Trust Edge use cases that are less sought by CISOs but demonstrate key vendor differentiation. End-to-end control provides visibility and governance across all network segments. Credential mapping unifies user identities across systems to simplify access policy enforcement. Unauthorized access detection and prevention protect against credential misuse and insider threats. Web content filtering from remote sites extends acceptable use policies.
Zero Trust Edge poised for growth
ZTE represents a pivotal shift in how enterprises secure their virtual teams and remote workers, assets, cloud environments and growing IoT networks. CISOs tell VentureBeat that legacy approaches to network, device, endpoint and identity security can’t keep up with the speed and complexity of cyberattacks. By converging networking and security, ZTE delivers a cloud-centric model that can be consumed as a service and paid for as an operating expense.
The variety of scope and approaches the 22 ZTE vendors mentioned in this report are taking to sell consolidation on their platforms shows how diverse the enterprise needs each is trying to meet. VentureBeat has learned that initial ZTE pilots are meeting expectations by supporting new digital-first revenue initiatives while closing the gaps in tech stacks that led to intrusion and breach attacks in the past.
In the near term, Forrester predicts larger enterprises will take a multivendor approach, integrating best-of-breed ZTE components from market leaders mentioned in their report. The core of ZTE’s simplification and consolidation value proposition makes it a compelling strategy for SMBs and midsize firms eager to standardize on a unified architecture. Demand is growing for a solution that can solve the most challenging multicloud and hybrid cloud security challenges, support remote work and zero trust initiatives. ZTE is well positioned to capitalize on these market dynamics.
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings.
[ad_2]
Source link





