
[ad_1]
Are you ready to bring more awareness to your brand? Consider becoming a sponsor for The AI Impact Tour. Learn more about the opportunities here.
Microsoft’s vision for zero trust security is galvanized around generative AI and reflects how identity and network access must constantly improve to counter complex cyberattacks.
Their many security announcements at Ignite 2023 reflect how they’re architecting the future of zero trust with greater adaptability and contextual intelligence designed in. The Microsoft Ignite 2023 Book of News overviews the new products announced this week at the event.
Zero Trust is core to Microsoft’s future
Throughout Ignite 2023 sessions, Microsoft clarified that their shift to a trust model is based on identity. Zero trust permeates their security strategy from now on, with their identity-centric approach to defining and delivering a security service edge (SSE) solution reflecting the scale they’re focused on achieving. Their SEE solution is predicated on using Microsoft Entra for internet, private access and Defender for cloud apps.
VB Event
The AI Impact Tour
Connect with the enterprise AI community at VentureBeat’s AI Impact Tour coming to a city near you!
“We just have to always assume breach, and that means continual monitoring. It means tons and tons of log files. It means everything needs to be constantly emitting data that helps if you can trust it,” Alex Simons, corporate vice president, Microsoft Identity & Network Access, said during the session “Accelerate your zero trust journey with unified access controls.”
Simon continued, “Our conditional access policy engine is the core of this. This gives you one place to be able to describe your corporate policy, who on what kind of device should be able to get to what kinds of your resources, when at what time, and what risk level, all those things all combined into one place.”
Simons emphasized Microsoft’s all-in commitment to the core principles of zero trust throughout the session. He explained how the core zero trust principles of verifying identities explicitly, using least privileged access, and assuming a breach has already occurred are the cornerstones of all zero trust, identity and network access, and security service edge development at Microsoft. Simon emphasized that Microsoft is all-in the trust fabric they have created where every identity, resource, request for resources, resource, and location are constantly verified.
Thursday’s zero trust session also explained how essential the conditional access policy engine and Microsoft Entra are to the future of zero trust at Microsoft. Entra permissions management is core to Microsoft’s zero trust security strategy because it enforces least privilege access and provides a unified interface for managing and monitoring permissions across multi-cloud environments.
Source: Accelerate your zero trust journey with unified access controls session, Microsoft Ignite 2023
Microsoft’s zero-trust vision takes shape
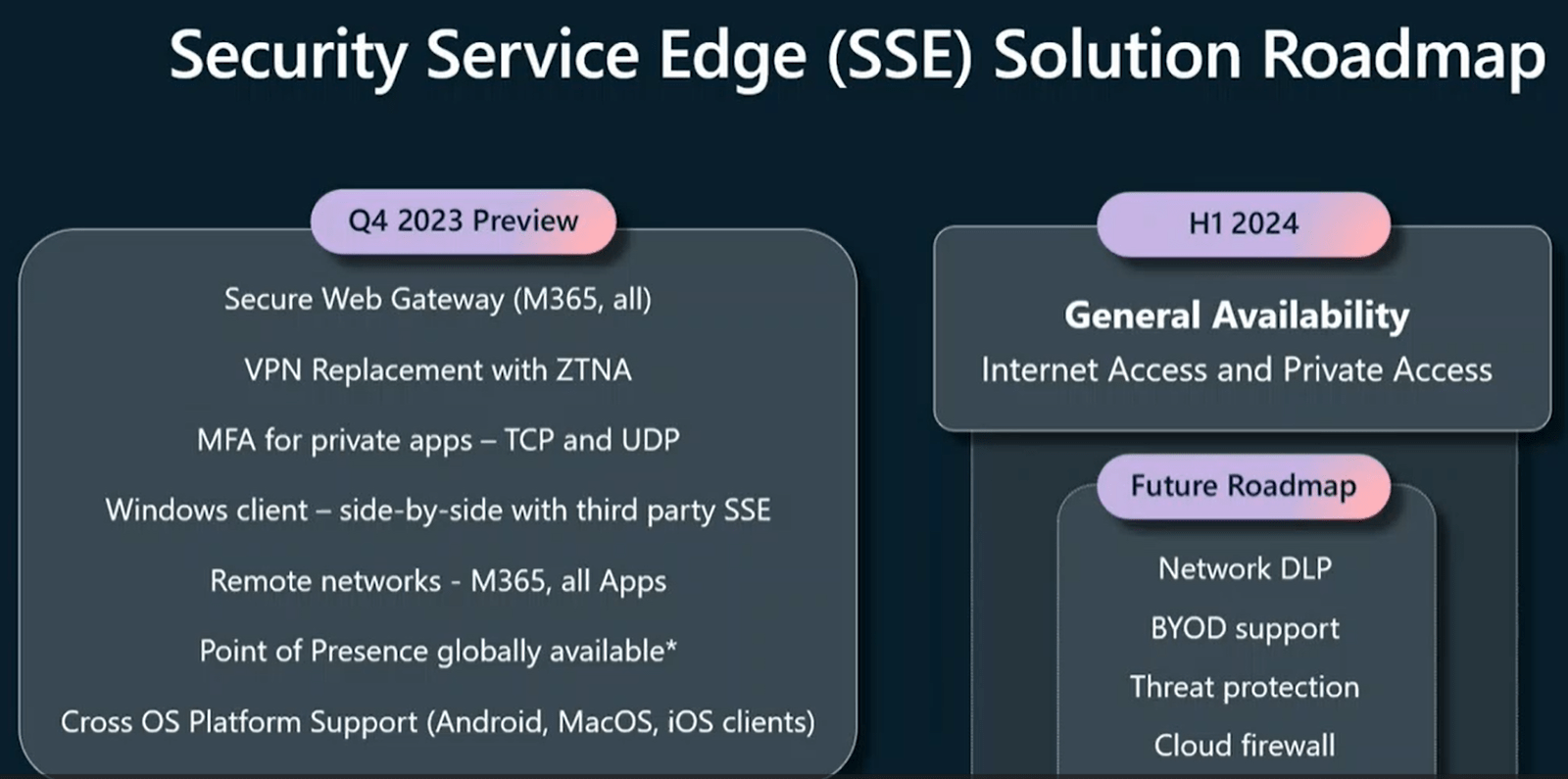
Sinead Odonovan, vice president of product management, Microsoft SSE, provided a thorough overview of the SSE platform and the solution roadmap the identity and network access teams are working towards.
Odonovan said the team aims to deliver six foundational elements of their zero-trust-based SSE solution roadmap this quarter, emphasizing secure web gateways and VPN replacements. In the first half of 2024, Microsoft Internet Access and Private Access will be launched for general availability. The future roadmap includes more solutions to strengthen their zero trust strategy, including improving network DLP, BYOD, threat protection and firewall support.
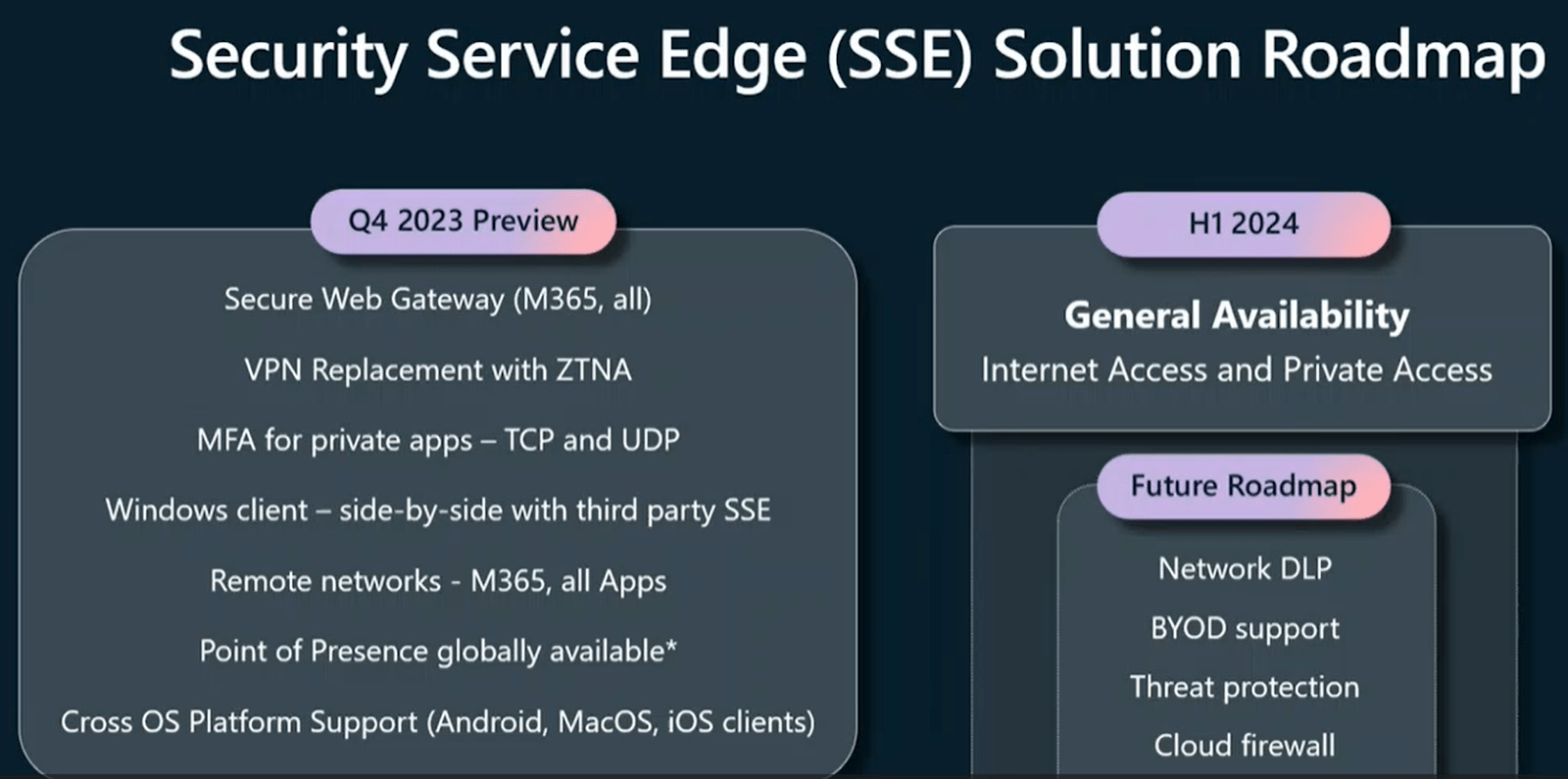
Source: Accelerate your zero trust journey with unified access controls session, Microsoft Ignite 2023
Microsoft launched its new Unified Security Operations Platform suite last week at Ignite 2023, integrating Microsoft Sentinel, Microsoft Defender XDR and Microsoft Security Copilot. By integrating SIEM, XDR and AI for real-time threat analysis and response, enterprise customers will have continuous monitoring and adaptive threat response, essential in zero trust, ensuring detection and mitigation of threats across network segments.
VentureBeat asked Forrester Principal Analyst Allie Mellen why Microsoft is consolidating security components now and entering the XDR market. Mellen said that “security practitioners deeply value the quality of detections available in XDR and the flexibility from SIEM. However, many are left wondering…why do I need two separate products in the SOC to do detection and response (XDR and SIEM)?” Mellin added,” This is important for a few reasons. The CISO is always looking for opportunities to consolidate data to save costs. With XDR and SIEM separate, data for detection and investigation is stored in two separate places, which is frustrating for security teams that already have to defend their exorbitant SIEM budget.”
Mellon also mentioned that security analysts want a unified analyst experience to simplify detection, investigation, and response in one place. With these two products previously lacking a unified analyst experience, it forced security analysts to pivot between two different views regularly, Mellen explained.
Mellen continued, “Bringing these two products together into a unified analyst experience simplifies security analyst workflow. They can now investigate and respond to incidents from XDR and SIEM in a single place while still maintaining the quality of detections from XDR and the flexibility of SIEM.”
Comparing how Ignite 2023 security announcements strengthen zero-trust security
Taken together, the security announcements at Ignite 2023 reflect the central role identity and network access have in Microsoft’s broader integration strategy. Microsoft provided examples of adopting SSE, Entra and InTune internally.
The full scope of Microsopft’s zero trust vision is taking shape. Gen AI contributes across a wide spectrum of use cases to help Microsoft customers pursue their approaches to a zero-trust framework. It’s encouraging to see Microsoft realize that its customers have heterogeneous environments that defy easy integration. The core technologies of their zero trust innovations are based on allowing for continuous monitoring, adaptive threat response and the fortification of all network segments against emerging cyber threats. The following table provides an overview of the security enhancements and their value to zero trust security.
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings.
[ad_2]
Source link





